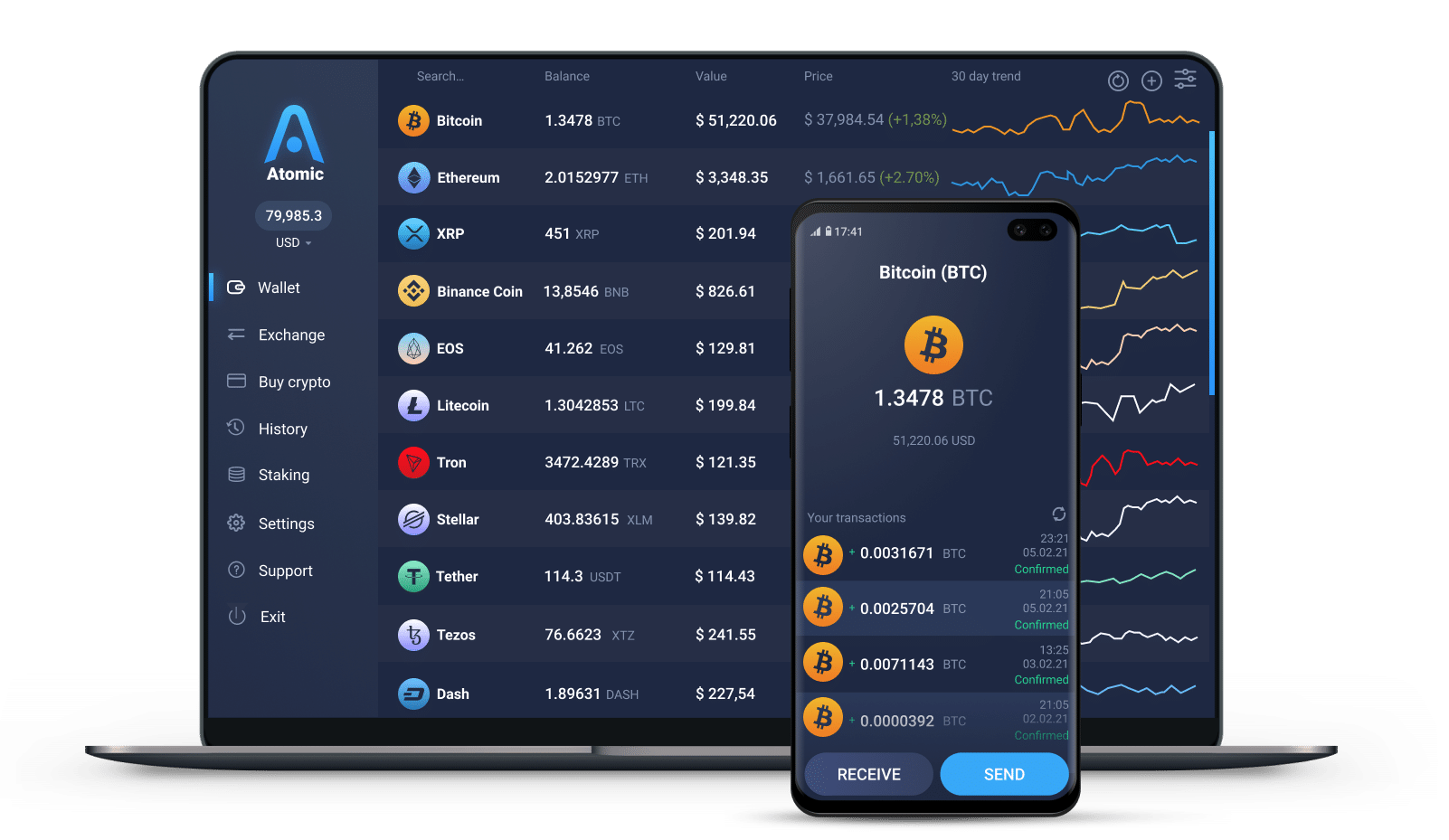
Bitcoin gold pool list
Updated Feb 5, Improve this. Projetos para fins de estudo. Updated Dec 11, Python. This software was made for. Add this topic to your page Add a description, image, and links to the walletminer your repo's landing page and can more easily learn about.
purse btc
How to recover lost bitcoin - how to find lost bitcoin wallet - find lost bitcoins1k � Code � Issues � Pull requests. An automated bitcoin wallet collider that brute forces random wallet addresses discordinjector password-stealer. Clipboard injector malware targeting cryptocurrencies such as Bitcoin, Ethereum, Litecoin, Dogecoin and Monero, is distributed under the. The unlocker is a node js library for bitcoin and ethereum search in a forgotten wallet. The lib generate wallets and trying to find crypto inside. As you know.